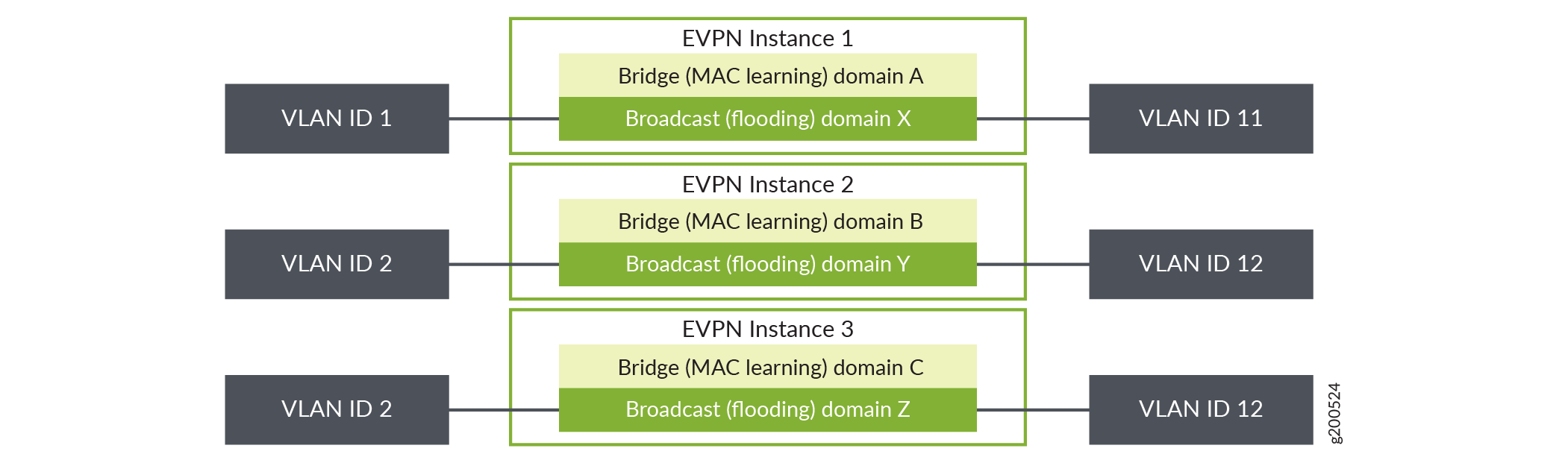
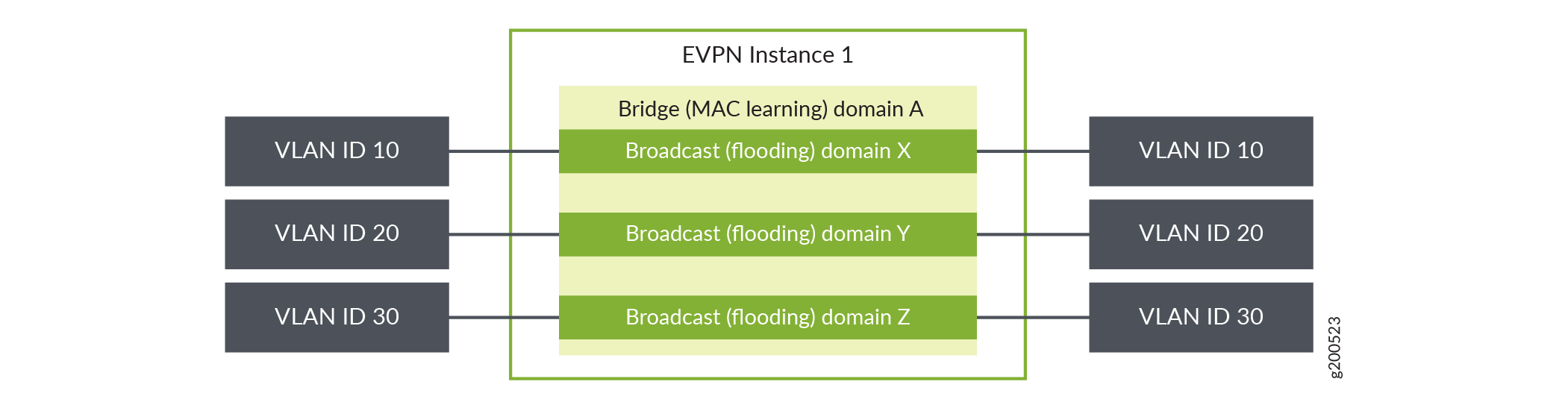
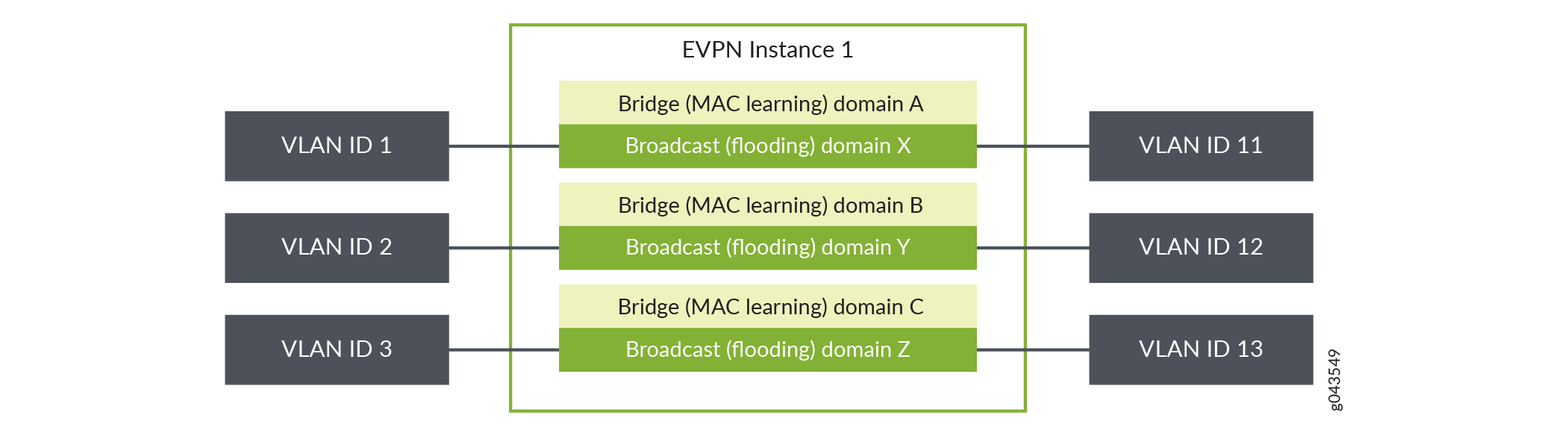
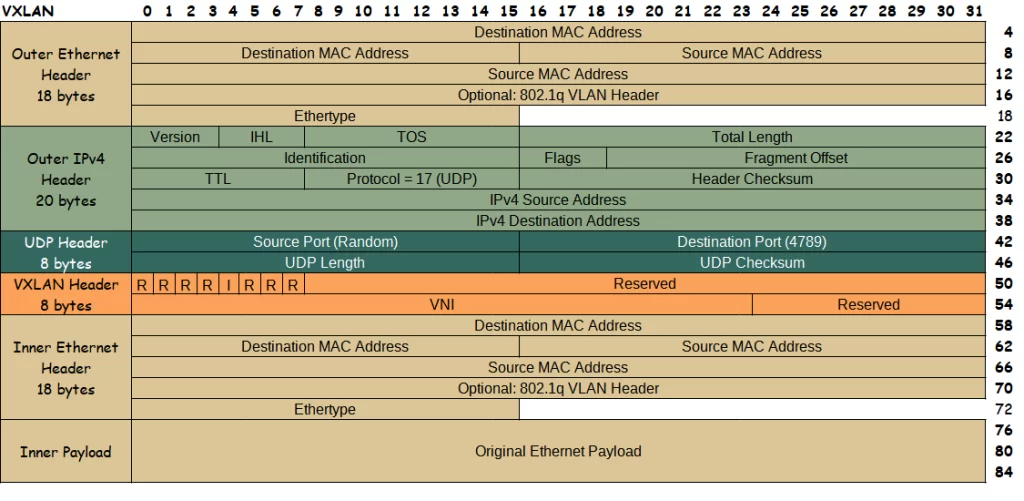
Interfaces
interfaces {
apply-groups [ interfaces-100g interfaces-10g interfaces-1g ];
et-0/0/24 {
apply-groups [ ESI-PORT ];
apply-groups-except MTU-VXLAN;
description "Internal: to sw2.et-0/0/51";
mtu 9216;
gigether-options {
fec fec91;
}
flexible-vlan-tagging;
encapsulation flexible-ethernet-services;
esi {
00:11:11:11:11:11:11:11:11:10;
}
unit 1850 {
encapsulation vlan-bridge;
vlan-id 1850;
}
unit 1851 {
encapsulation vlan-bridge;
vlan-id 1851;
}
unit 1852 {
encapsulation vlan-bridge;
vlan-id 1852;
}
unit 1853 {
encapsulation vlan-bridge;
vlan-id 1853;
}
}
}
Routing Instance
routing-instances {
evpn-100 {
instance-type mac-vrf;
protocols {
evpn {
encapsulation vxlan;
extended-vni-list all;
}
}
vtep-source-interface lo0.0;
service-type vlan-aware;
route-distinguisher 10.255.252.0:100;
vrf-import IMPORT-POLICY-100;
vrf-target target:64999:100;
vlans {
bd-100-1850 {
vlan-id 1850;
interface et-0/0/24.1850;
vxlan {
vni 1850;
encapsulate-inner-vlan;
}
}
bd-100-1851 {
vlan-id 1851;
interface et-0/0/24.1851;
vxlan {
vni 1851;
encapsulate-inner-vlan;
}
}
bd-100-1852 {
vlan-id 1852;
interface et-0/0/24.1852;
vxlan {
vni 1852;
encapsulate-inner-vlan;
}
}
bd-100-1853 {
vlan-id 1853;
interface et-0/0/24.1853;
vxlan {
vni 1853;
encapsulate-inner-vlan;
}
}
}
}
}
Policies
policy-options {
policy-statement EXPORT-POLICY-100 {
term ROUTE-TARGET {
then {
community add RT100;
}
}
}
policy-statement IMPORT-POLICY-100 {
term ROUTE-TARGET-iBGP {
from community RT100-iBGP;
then accept;
}
}
community RT100 members [ target:65001:100 target:64999:100 ];
community RT100-eBGP members target:65001:100;
community RT100-iBGP members target:64999:100;
}
Groups
groups {
ESI-PORT {
interfaces {
<*> {
esi {
all-active;
}
}
}
}
interfaces-100g {
<et-*> {
description "Reserved for 100 GbE port speeds";
disable;
}
}
interfaces-10g {
<xe-*> {
description "Reserved for 10 GbE port speeds";
disable;
}
}
interfaces-1g {
<ge-*> {
description "Reserved for 1 GbE port speeds";
disable;
}
}
}
Forwarding options
forwarding-options {
evpn-vxlan {
shared-tunnels;
}
}
Protocols
protocols {
l2-learning {
decapsulate-accept-inner-vlan;
}
bgp {
group ipv6-backbone {
family evpn {
signaling;
}
}
group ipv4-backbone {
family evpn {
signaling;
}
}
}
}