Table of Contents
RFC’s
- RFC 9161 – Operational Aspects of Proxy ARP/ND in EVPN
- RFC 9136 – IP Prefix Advertisement in EVPN
- RFC 9135 – Integrated Routing and Bridging in EVPN
- RFC 9014 – Interconnect Solution for EVPN Overlay Networks
- RFC 8584 – Framework for EVPN Designated Forwarder Election Extensibility
- RFC 8365 – A Network Virtualization Overlay Solution Using EVPN
- RFC 7623 – PBB Combined with EVPN
- RFC 7432 – BGP MPLS-Based EVPN
- RFC 7364 – Problem Statement: Overlays for Network Virtualization
- RFC 7348 – VXLAN: A Framework for Overlaying Virtualized L2 over L3
- RFC 7209 – Requirements for EVPN
- RFC 7080 – VPLS Interoperability with PBB
- RFC 4377 – OAM Requirements for MPLS Networks
Drafts
YouTube
- Revisiting BGP Data Center Design – 2023-08-31
- EVPN multi-homing: an open alternative to MLAG (Nokia TechTalks) – 2023-05-15
- EVPN Route Types (Nokia TechTalks) – 2023-05-15
- EVPN Multi-homing in 10 (Nokia TechTalks) – 2023-04-12
- EVPN Route Types in 10 (Nokia TechTalks) – 2023-04-12
- Using Gateways for SRv6 and MPLS Interworking (Nokia) – 2022-04-21
- Seamless Data Center Interconnect options using EVPN & various tunnel stitching {NANOG} – 2022-10-26
- EVPN Deep Dive – All EVPN Route Types explained by Orhan Ergun and Toni Pasanen – 2020-04-28
- Understanding ASICs for Network Engineers (Pete Lumbis) {NANOG} – 2020-02-21
- SONiC: Open Source NOS in Data Center {NANOG} – 2019-11-05
- Understanding ASICs For Network Engineers (Pete Lumbis) {Packet Pushers} – 2019-06-17
Playlists
- Intro To EVPN With Tony Bourke – 2021-06-26
- EVPN MPLS on Cisco IOS-XE and Cisco IOS-XR – 2023-05-11
- Between 0x2 Nerds – Several EVPN episodes (Podcast format)
Routing Daemons
- docs.frrouting.org/en/latest/evpn.html
- github.com/osrg/gobgp/blob/master/docs/sources/evpn.md
- blog.vyos.io/evpn-vxlan-vyos
Linux Hypervisors
Commercial Vendors
- juniper.net/documentation/en_US/tech-center/topics/concept/evpn-vxlan-technology.html
- juniper.net/documentation/us/en/software/junos/evpn-vxlan/topics/concept/evpn-bgp-multihoming-overview.html
- juniper.net/documentation/us/en/software/junos/evpn-vxlan/index.html
- ciscolive.com/c/dam/r/ciscolive/emea/docs/2019/pdf/LTRSPG-2968.pdf (see slide 32 for EVPN Route Cheat Sheet)
- juniper.net/documentation/us/en/software/junos/evpn-vxlan/topics/concept/pbb-evpn-integration-for-dci-overview.html
- juniper.net/documentation/us/en/software/junos/evpn-vxlan/topics/topic-map/vxlan-ipv6-underlay-overview.html
Blog Posts
- listed.to/@techtrips/15700/l3vpn-with-frr-and-evpn-vxlan-on-linux (2020-06-14)
- vincent.bernat.ch/en/blog/2017-vxlan-bgp-evpn
- bgphelp.com/2017/05/05/evpn-mpls-port-based-vlan-aware-bundle-service/
- tgregory.org/2016/06/04/evpn-in-action-1/
- tgregory.org/2016/06/11/inter-vlan-routing-mobility/
- tgregory.org/2016/06/16/evpn-single-active-redundancy/
- tgregory.org/2016/06/21/evpn-all-active-multihoming/
- tgregory.org/2016/11/15/evpn-vs-pbb-evpn-and-massive-scale/
Side notes
- Bird2 does not (yet) have EVPN SAFI support on the ROADMAP
- MikroTik RouterOS has no support. Unknown if it will ever be implemented.
- IANA – Address Family Numbers (AFI’s)
- IANA – Subsequent Address Family Identifiers (SAFI) Parameters
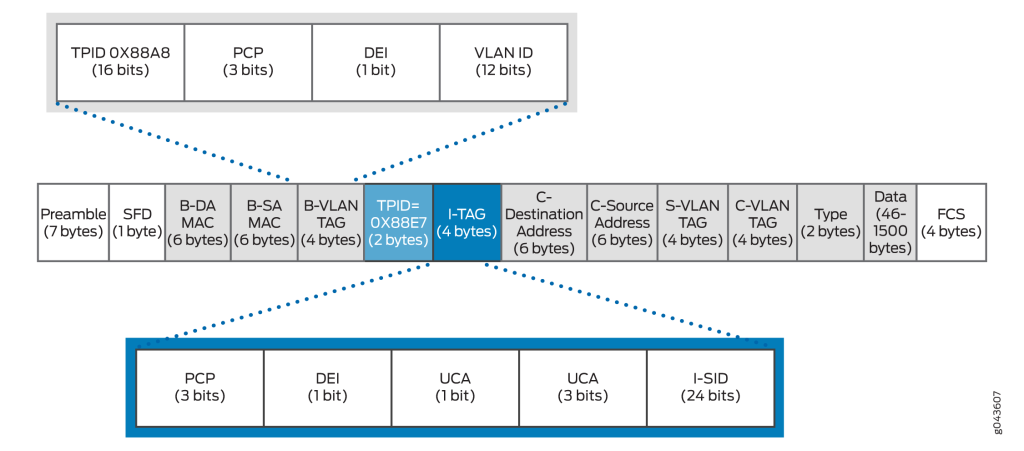
VXLAN Packet
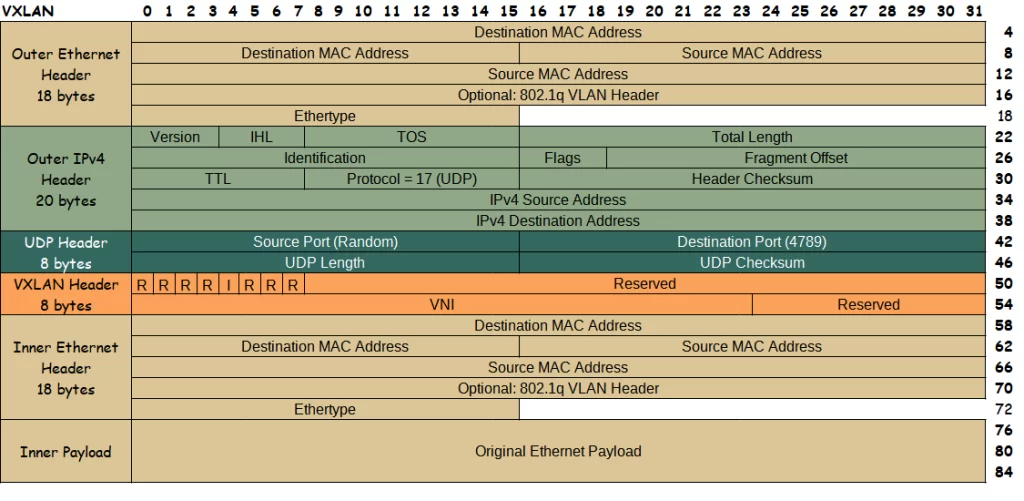
PBB Packet Format